Unlimited Residential Proxies That Actually Scale Without Surprises
“Unlimited residential proxies” usually means unlimited billing in one dimension while other limits still exist in production: concurrency caps, port caps, speed shaping, session TTL, fairness enforcement, and destination-specific throttles. If you buy the plan without measuring these, you’ll discover them mid-soak.
If you need a concrete starting point for how an unlimited plan is typically packaged, Unlimited Residential Proxies is a useful reference for mapping features to testable constraints.
What to do instead of guessing:
- Translate every “unlimited” claim into numbers
- Validate with five gates and keep an evidence bundle
- Operate inside risk boundaries, treating 429 and fair-use controls as first-class signals
Reader map
This guide is for operators doing:
- Large-scale scraping and data collection
- Ad verification and geo QA
- Multi-account operations where session stability matters
- Continuous monitoring, price tracking, and content diffing
- Bursty workloads with retries and long-tail latency risk
Proxy basics are assumed.
What most “unlimited” pages fail to tell you
Many “unlimited bandwidth residential proxy” pages describe benefits but don’t define the term across the dimensions that actually break systems:
- Bandwidth billing vs real throughput
- Requests per second vs concurrency
- Session length vs forced rebinding
- “Unlimited IPs” vs effective clean pool for your targets
- Fair use and abuse controls that silently reshape performance
Google’s own guidance on creating helpful, reliable content is a good sanity check for your procurement process: look for specificity, constraints, and verifiable claims, not adjectives. Creating helpful, reliable, people-first content
What unlimited means in real proxy plans

Unlimited bandwidth is not unlimited throughput
Unlimited bandwidth usually means you are not billed per GB. It does not guarantee:
- Sustained Mbps per port
- Account-level throughput floors
- Stable p95 latency under load
- No shaping during peak hours
Common implementations you’ll see in the field:
- Per-port shaping, such as “each port behaves like a small pipe”
- Account-level fairness, where aggregate throughput flattens beyond a threshold
- Adaptive shaping that reacts to error-rate and retry storms
If a vendor won’t state a throughput envelope, assume you must discover it.
Unlimited traffic is not unlimited requests
Requests are constrained by:
- Concurrency and connection reuse
- Destination rate limits
- Provider fairness rules
- Your retry policy and timeout settings
An “unlimited traffic residential proxy” plan can still be effectively “unlimited traffic at N concurrent sessions.”
Unlimited concurrency must be a number
If the plan claims unlimited concurrency but won’t name a limit, treat it as “unknown concurrency” and test it.
The real ceiling typically shows up as one of these patterns:
- Hard cap: new connections fail or auth begins failing at a fixed threshold
- Soft cap: queueing rises, p95 explodes, then timeouts dominate
- Per-destination cap: concurrency works across many domains but collapses on one target
Unlimited sessions still have session TTL
Unlimited residential plans still manage risk using session policy:
- Sticky window rotation, often minutes
- Forced rebinding under load
- TTL resets based on inactivity or abuse heuristics
If you run login-adjacent QA or multi-account flows, session TTL is a first-order requirement.
Unlimited ports still hide port and auth caps
Even if bandwidth is “unlimited,” vendors often cap:
- Ports or endpoints
- Credentials or sub-users
- Whitelisted IP entries
- Token-level RPS
These caps determine whether you can scale workers independently or need coordination.
Fair use always exists
Every sustainable “unlimited” plan has fairness and abuse control. This is not optional infrastructure; it’s the difference between a stable service and a noisy-neighbor meltdown. Expect enforcement via shaping, throttling, or temporary blocks.
Unmetered vs unlimited proxies and why labels mislead
Treat “unmetered” and “unlimited” as marketing wrappers. What matters is what resource is being metered:
- Data: billed per GB
- Capacity: billed per port, thread, or concurrency tier
- Time: billed per day or month with guardrails
- Hybrid: “unlimited data” but strict concurrency and throughput ceilings
Your job is to identify the real metering axis, then validate the operational envelope.
Define unlimited precisely as an operator spec
Use this checklist to rewrite a vendor’s plan into testable statements. The key is to separate billing from enforcement.
Bandwidth and throughput
- Billing: unmetered GB, yes or no
- Enforcement: sustained Mbps per port and per account
- Shaping: fixed, adaptive, or peak-hour only
Requests and concurrency
- Max concurrent TCP connections
- Max concurrent sessions per credential
- Per-destination concurrency ceilings
Ports and auth
- Max ports or endpoints
- Max credentials, sub-users, or tokens
- Any per-token rate limit
Session behavior
- Sticky window duration
- Forced rebinding triggers
- Maximum practical session hours under load
Pool reality
- Unique egress IPs per hour in your target class
- Geo and ASN constraints that reduce effective pool
- Burn dynamics in soak tests
Fair use and enforcement
- What triggers throttling or suspension
- Whether enforcement is reversible via pacing changes
- Whether penalties spill across unrelated targets
If you need a baseline definition of residential proxy types and how they differ in practical constraints, Residential Proxies is a clean reference point for standardizing your spec vocabulary.
The decision framework for unlimited plans vs per-GB plans
Start from economics, not adjectives
Compare plans using two operator metrics:
- Cost per successful response
- Cost per stable session hour
Because retries, timeouts, and session churn are the hidden multipliers.
Cost per successful response
- P = monthly price
- S = successful responses you accept after content checks
- Cost per success = P / S
If S collapses under soak, the plan is not “cheap” even if bandwidth is unlimited.
When unlimited residential plans are the right choice
Unlimited bandwidth plans often win when:
- You do high request volume with small-to-medium payloads
- Workload is bursty and hard to forecast
- You can tolerate rotation and don’t need long-lived identity
- Targets are commodity public pages with moderate defenses
- Your retry inflation is controlled with backoff and caching
Long-tail query coverage you should consider here:
- unlimited residential proxies for scraping at scale
- unlimited bandwidth residential proxies for monitoring
- residential proxies unlimited traffic for price tracking
When per-GB plans win
Per-GB plans often win when:
- Payloads are large or assets must be enabled
- You need long, stable sessions
- You care about predictability over raw volume
- You can forecast traffic and optimize caching
Five-minute break-even math
Estimate average KB per request:
- API JSON or headers-heavy: 10–50 KB
- Typical HTML without heavy assets: 100–800 KB
- Heavy pages with assets: 1–5+ MB
Monthly GB ≈ (requests × avg_KB) / (1024 × 1024)
Then apply retry inflation:
- Effective requests = base requests × (1 + retry_rate)
If retry_rate becomes 2–5x during bad windows, per-GB cost can spike, and “unlimited bandwidth” may be economically safer—provided concurrency and throughput are sufficient.
If you want the plan comparison to be non-hand-wavy, anchor the economics to an explicit price surface like Unlimited Residential Proxies Pricing and then compute cost per success from your measured results.
The engineer’s validation playbook
Your goal is to validate the plan as a system: throughput, concurrency, session stability, and enforcement behavior. Do this before you wire it into production.
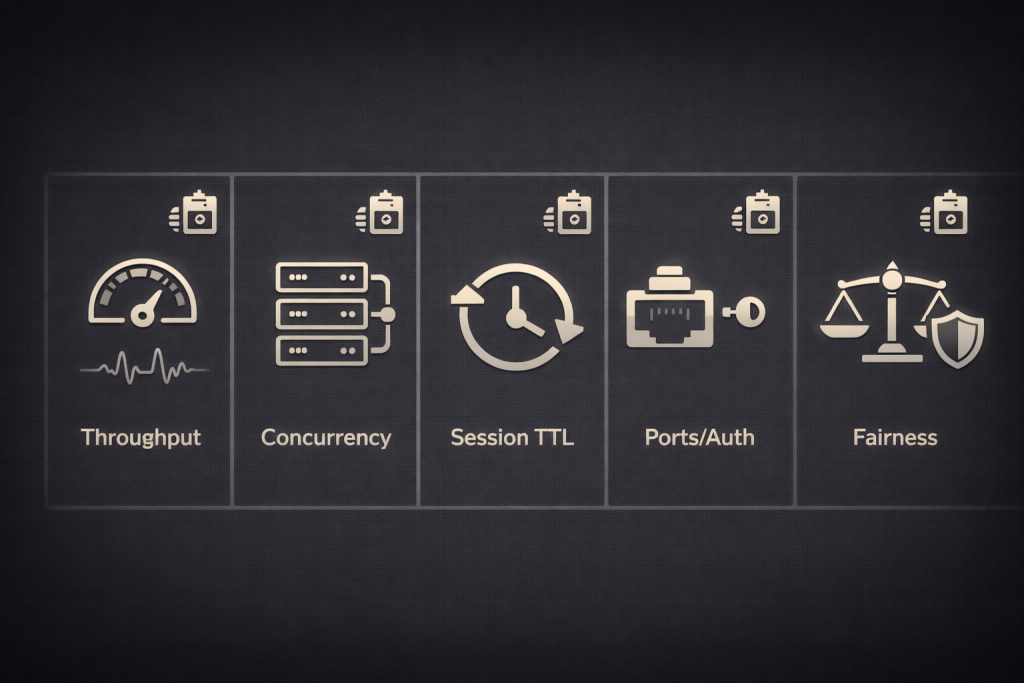
Test setup principles
- Use keep-alive and connection pooling so you don’t mistake handshake overhead for proxy limits.
- Use exponential backoff with jitter so your client doesn’t create retry storms.
- Test one target class at a time; mixing five domains destroys interpretability.
MDN is a helpful secondary reference for the same status code. HTTP 429 Too Many Requests
Gate 1: Throughput and shaping
Goal: detect speed shaping and throughput ceilings.
Method:
- Run fixed-load tests at low, medium, high concurrency.
- Track Mbps, TTFB, p50/p95 latency, and error rate.
Pass signals:
- Throughput increases with concurrency until destination-side constraints appear.
- p95 remains stable enough for your SLO.
Fail signals:
- Throughput flatlines early while p95 rises.
- Sawtooth throughput patterns repeating on a fixed interval.
- Strong per-connection ceilings across ports.
Artifacts:
- Time series of Mbps and connections
- Latency histograms
- Sample failed responses with headers
Gate 2: Concurrency ceiling and queue behavior
Goal: find the real concurrency cap and whether enforcement is hard or soft.
Method:
- Ramp concurrency in steps: 10 → 25 → 50 → 100 → 200.
- Hold each step for 5–10 minutes.
Pass signals:
- A documented ceiling that matches reality, or a high enough limit for your plan.
- Graceful degradation with actionable signals.
Fail signals:
- Silent queueing that turns into timeout storms.
- Sudden auth failures beyond a threshold.
- Throttling that mimics destination issues.
Artifacts:
- Ramp schedule
- Per-minute success and error counts
- Raw examples of failures at the threshold
Gate 3: Session stickiness and TTL behavior
Goal: verify sticky windows and forced rebinding triggers.
Method:
- Assign one session key per worker.
- Sample egress IP periodically.
Pass signals:
- Session holds for expected window, rotation is predictable.
Fail signals: - Random rebinding under load, short TTL despite claims.
Artifacts:
- Session id to egress IP timeline
- Rebinding timestamps correlated with error spikes
Gate 4: Port and auth caps
Goal: discover scaling caps that block horizontal worker growth.
Method:
- Add workers until the system fails in a repeatable way.
Watch for:
- Auth throttles, credential caps, port ceilings, whitelist limits.
Artifacts:
- Auth error payloads
- Timestamps and scale level at failure
- Any control-plane messages
If you need to standardize how your clients negotiate and what protocol-level choices affect scaling behavior, Proxy Protocols is a useful reference for aligning implementation details across teams.
Gate 5: Fair use enforcement behavior
Goal: understand what happens as you approach “noisy neighbor” territory without doing abusive activity.
Method:
- Keep targets permitted and non-destructive.
- Push high but reasonable request rates.
- Compare normal pacing vs stressed pacing.
Pass signals:
- Enforcement is transparent and reversible via pacing.
Fail signals: - Opaque penalties that persist after load reduction.
- Spillover across unrelated targets.
Artifacts:
- A/B time series of rate, success, 429s, timeouts
- Response headers, including Retry-After where present
Evidence bundle checklist
Capture these every time you evaluate “unlimited residential proxy best practices” in a new environment:
- Test plan with ramp schedule
- Client config: timeouts, retries, jitter, keep-alive, pooling
- Per-minute metrics: attempts, successes, 429s, 403s, 5xx, timeouts
- Latency histograms: p50, p90, p95, p99
- Session timeline: session id → egress IP
- At least 20 raw failure samples with headers
- Notes on DNS and TLS behavior
- Pass/fail write-up per gate
MaskProxy is a practical way to organize these trials because it forces you to describe “unlimited” as measurable gates rather than as a plan label.
Risk boundaries and operating safely

Unlimited plans are often used for automation at scale. That increases the chance your traffic resembles known automated threats. The OWASP Automated Threats to Web Applications project is a useful taxonomy for understanding where automation becomes harmful or abusive. OWASP Automated Threats to Web Applications
Practical guardrails:
- Treat 429 as a hard feedback loop: slow down, back off, respect Retry-After. Error 429
- Use domain and endpoint concurrency budgets.
- Cache aggressively to avoid repeated fetches.
- Avoid tight retry loops and synchronized bursts.
- Separate pools by target class to prevent one defense response from poisoning unrelated workloads.
- Keep scope and purpose limitation explicit in your runbooks.
Troubleshooting runbook

| Symptom | Likely cause | First fix | Artifact |
|---|---|---|---|
| Throughput flatlines as concurrency increases | Shaping or per-port ceiling | Compare per-port vs account-level Mbps, add ports, request explicit throughput tier | Mbps and connection count time series |
| p95 explodes and timeouts climb | Provider queueing or overloaded POP | Lower concurrency, shard across endpoints or POPs, tighten timeouts and add jitter | Latency histogram and timeout timeline |
| Sudden 429 spike at steady load | Destination rate limit or fairness enforcement | Cut concurrency, reduce RPS, honor Retry-After | Raw 429 responses with headers |
| Sessions break mid-flow | Session TTL too short or forced rebinding | Reduce churn, lower per-session concurrency, request longer sticky window | Session id to egress IP timeline |
| IPs repeat far more than expected | Constrained geo pool or sticky window behavior | Widen geo and ASN constraints, adjust rotation mode | Unique IP count per hour per geo |
| New workers fail auth when scaling | Auth cap or token throttling | Reduce parallel auth bursts, consolidate credentials, request higher quotas | Auth errors and timestamps |
| Success rate decays during soak | Reputation burn or enforcement triggers | Slow down, rotate pools, increase cache hit rate, separate targets | Soak curve of success and error mix |
Buyer checklist
Force numeric answers:
- Sustained account-level throughput in Mbps
- Per-port throughput ceiling and whether shaping is adaptive
- Max concurrent connections and whether it’s per account, per endpoint, or per destination
- Sticky session window and forced TTL under load
- Port caps, credential caps, whitelist limits
- Enforcement behavior under fair use: shaping, throttling, suspension, reversibility
- Telemetry exposure: error codes, POP routing visibility, rate-limit signals
- Trial differences: what is limited in trial vs paid
Closing
An “unlimited residential proxies” plan can be the best economic choice for high-volume operators, but only if you translate the claim into a measurable spec and validate it before production. When you need frequent rotation with predictable operational behavior, Rotating Residential Proxies is the natural comparison point for choosing the right rotation and session model.
Daniel Harris is a Content Manager and Full-Stack SEO Specialist with 7+ years of hands-on experience across content strategy and technical SEO. He writes about proxy usage in everyday workflows, including SEO checks, ad previews, pricing scans, and multi-account work. He’s drawn to systems that stay consistent over time and writing that stays calm, concrete, and readable. Outside work, Daniel is usually exploring new tools, outlining future pieces, or getting lost in a long book.
FAQ
1.What are unlimited residential proxies
Usually: residential egress where billing is not metered by GB. You still have constraints in throughput, concurrency, session TTL, port caps, and fair-use enforcement.
2.What does unlimited bandwidth residential proxy really mean
It usually means “no per-GB billing.” It does not guarantee unlimited speed. Validate shaping with throughput and p95 metrics.
3.Unmetered vs unlimited proxies
Ignore the label and identify what’s being metered: data, capacity, or time. Validate the enforcement envelope with measurable tests.
4.Residential proxies with unlimited traffic is that truly unlimited
It usually means unmetered billing, not infinite requests. Your practical ceiling is often concurrency plus fairness and destination rate limits.
5.What are the best practices for unlimited residential proxies
Define “unlimited” precisely, validate with gates, capture evidence, pace responsibly, and treat 429 as a stop signal rather than as a challenge.